Standard Managed Service ProvidersMost IT Managed Services Providers (MSPs) use the same, low-privacy software ownership model as everyone else: they punt it all into the cloud. So when it comes to managing your organization’s IT documentation, support incident information, infrastructure passwords, and all of your MPS’s internal documentation and communications? Well, if you look at it honesty, thousands and thousands of people do. Their internal technicians and support personnel, certainly. Most MSPs do not segment their internal support staff into groups, so that every technician has access to the data for every customer. But it’s not just them – it’s the companies they outsource to. Their Professional Services Automation system that handles proposals, ticketing, job tracking, and billing is almost certainly sitting in the cloud, so the technicians and support staff for that company also has access to all of this data. The same with their Remote Monitoring and Managing products that control and provide remote access to your computers and servers. The same with their Password Management, their email, calendaring, file sharing, messaging, etc. – it’s all in the cloud, and all of those service provider technicians can take a peek. But that’s not the last layer – virtually all of these SaaS companies are hosted on Big Data platforms like MS Azure, Google Cloud, or Amazon Web Services – so the technical staff of those systems (who number in the tens of thousands) can peek in on this data as well. Everyone promises up and down that they will never abuse this trust, and most of them won’t. But it only takes one bad apple to ruin everything, and at the end of the day there are upwards of a hundred thousand technicians and customer support staff involved, most in countries chosen for the low wages that can be paid to these workers. It’s not just spying – it’s also criminal hacking. Security compromises and data destruction at larger layers here offer incredible return-on-investment for ransomware gangs and other cybercriminals, not to mention hostile governments. We have said for years that centralizing so much high-value information is insanity. It’s too many eggs in one basket. We’re well past the point where it’s worth spending many millions of dollars to break into these larger layers. We would argue it’s worth spending hundreds of millions to attack the biggest ones, and none of these hyper-scaled companies can withstand that kind of attack. |
 |
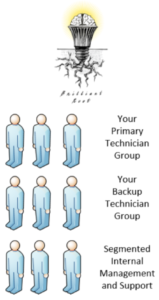
The BrilliantRoot DifferenceAt BrilliantRoot, we chose a different path, one that provides massively more privacy and security for our customers. It’s really very simple: we own our own tools, we run them on our own servers, and we support them with our own technicians. We then segment our customers’ information into internal groups within our organization, based on the following design goals: no matter how large we grow, no more than a dozen people can access any customer’s information. If one internal group is compromised, the compromise is contained and does not affect other groups. On the customer side, we offer the same thing: keeping your data and tools on your own servers. minimizing ROI for cybercriminals. Does it cost a bit more? Sure, but not a crazy amount. At BrilliantRoot, we put our customer’s privacy and security ahead of nickel-and-diming our overhead. |
 |